

A、 Ensure that the source and destination vCenter instances share the same Key Management Server (KMS).
B、 Ensure that Encrypted vMotion Is turned off for the VM
C、 Ensure that the VM is encrypted before attempting the migration
D、 Ensure that the VM is powered off before attempting the migration.
E、 Ensure that the source and destination vCenter Servers have a different Key Management Server (KMS).
F、
G、
H、
I、
J、
答案:AC
解析:解析: To ensure a successful migration of an encrypted VM to a secure environment, the administrator needs to ensure that the source and destination vCenter instances share the same Key Management Server (KMS), which provides encryption keys for both environments; and ensure that the VM is encrypted before attempting the migration, which allows preserving its encryption status during vMotion.为了确保加密虚拟机成功迁移到安全环境,管理员需要确保源和目标vCenter实例共享同一个密钥管理服务器(KMS),该服务器为两个环境提供加密密钥;并确保在尝试迁移之前对虚拟机进行加密,这样可以在vMotion过程中保留其加密状态。



A、 Ensure that the source and destination vCenter instances share the same Key Management Server (KMS).
B、 Ensure that Encrypted vMotion Is turned off for the VM
C、 Ensure that the VM is encrypted before attempting the migration
D、 Ensure that the VM is powered off before attempting the migration.
E、 Ensure that the source and destination vCenter Servers have a different Key Management Server (KMS).
F、
G、
H、
I、
J、
答案:AC
解析:解析: To ensure a successful migration of an encrypted VM to a secure environment, the administrator needs to ensure that the source and destination vCenter instances share the same Key Management Server (KMS), which provides encryption keys for both environments; and ensure that the VM is encrypted before attempting the migration, which allows preserving its encryption status during vMotion.为了确保加密虚拟机成功迁移到安全环境,管理员需要确保源和目标vCenter实例共享同一个密钥管理服务器(KMS),该服务器为两个环境提供加密密钥;并确保在尝试迁移之前对虚拟机进行加密,这样可以在vMotion过程中保留其加密状态。


A. Create a hot clone of the physical server using VMware vCenter Converter.
B. Create a cold clone of the physical server using VMware vCenter Converter.
C. Restore the guest OS from a backup.
D. Use storage replication to replicate the guest OS and application.
E.
F.
G.
H.
I.
J.
解析:解析:Option B is correct because it allows the administrator to create a cold clone of the physical server using VMware vCenter Converter, which will create an image of the guest OS and application that can be moved to this remote data center without requiring network connectivity or affecting the application’s data. Option A is incorrect because creating a hot clone of the physical server using VMware vCenter Converter will require network connectivity and may affect the application’s data due to changes during conversion. Option C is incorrect because restoring the guest OS from a backup will require network connectivity and may not include the latest changes in the application. Option D is incorrect because using storage replication to replicate the guest OS and application will require network connectivity and may not be feasible for a physical server.选项B是正确的,因为它允许管理员使用VMware vCenter Converter创建物理服务器的冷克隆,这将创建来宾操作系统和应用程序的映像,这些映像可以移动到该远程数据中心,而不需要网络连接或影响应用程序的数据。选项A不正确,因为使用VMware vCenter Converter创建物理服务器的热克隆需要网络连接,并且可能会由于转换期间的更改而影响应用程序的数据。选项C不正确,因为从备份恢复来宾操作系统需要网络连接,并且可能不包括应用程序中的最新更改。选项D不正确,因为使用存储复制来复制来宾操作系统和应用程序需要网络连接,对于物理服务器来说可能不可行。
A. vSphere Distributed Resource Scheduler (DRS)
B. vSphere vMotion
C. vSphere Faull Tolerance
D. vCLS Retreat Mode
E.
F.
G.
H.
I.
J.
解析:解析: The feature that can be used to avoid the use of Storage vMotion on the vCLS VMs when performing maintenance on a datastore is vCLS Retreat Mode, which allows temporarily removing the vCLS VMs from the cluster without affecting the cluster services.在数据存储上执行维护时,可用于避免在vCLS虚拟机上使用Storage vMotion的功能是vCLS撤退模式,该模式允许临时从群集中删除vCLS虚拟机,而不会影响群集服务
A. vSphere Virtual Machine Encryption
B. vSphere Visualization-Based Security
C. Virtual Intel Software Guard Extensions (vSGX)
D. Virtual Trusted Platform Module (vTPM)
E.
F.
G.
H.
I.
J.
解析:
A. Set appropriate permissions on the virtual machine.
B. Create a virtual machine customization specification.
C. Upgrade the virtual hardware
D. Convert the virtual machine to a template.
E. Take a snapshot of the virtual machine.
F.
G.
H.
I.
J.
解析:解析: Option B and D are correct because they allow the administrator to create a virtual machine customization specification, which can be used to customize guest operating system settings for multiple virtual machines, and convert the virtual machine to a template, which can be used to create full clones of server workloads.Option A is incorrect because assigning appropriate permissions on the virtual machine does not prepare it for deployment for multiple users. Option C is incorrect because upgrading the virtual hardware does not prepare it for deployment for multiple users. Option E is incorrect because taking a snapshot of the virtual machine does not prepare it for deployment for multiple users. References:解释选项B和D是正确的,因为它们允许管理员创建虚拟机自定义规范,该规范可用于为多个虚拟机自定义来宾操作系统设置,并将虚拟机转换为模板,该模板可用于创建服务器工作负载的完整克隆。选项A不正确,因为在虚拟机上分配适当的权限并不能为多用户部署做好准备。选项C不正确,因为升级虚拟硬件不会为多用户部署做好准备。选项E不正确,因为拍摄虚拟机的快照并不能为多用户部署做好准备。
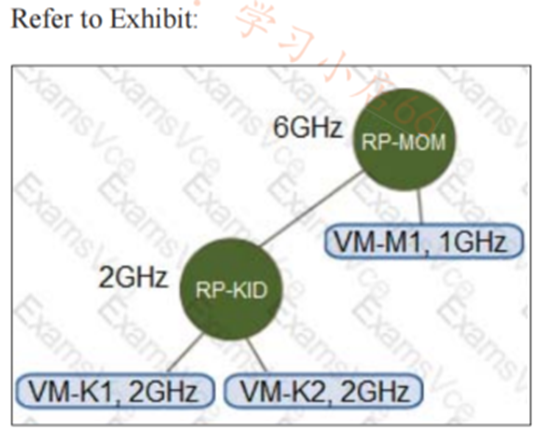 An environment has the following configuration: •Resource Pool “RP-MOM? has a reservation of 6GHz and one running virtual machine (VM) ”VM-M1? With 1 GHz reserved •Resource Pool ^RP-KID? has a reservation of 2GHz, and expandable reservations is activated The administrator creates two VMs, “VM-K1? and 'VM-K2?, in the ''RP-KID? resource pool with 2GHz reserved for each, and turns on “VM-M1 ?
An environment has the following configuration: •Resource Pool “RP-MOM? has a reservation of 6GHz and one running virtual machine (VM) ”VM-M1? With 1 GHz reserved •Resource Pool ^RP-KID? has a reservation of 2GHz, and expandable reservations is activated The administrator creates two VMs, “VM-K1? and 'VM-K2?, in the ''RP-KID? resource pool with 2GHz reserved for each, and turns on “VM-M1 ?
A. The administrator must deactivate expandable reservations to turn on VM-K2
B. The administrator can create a third VM ( VM-K3?) at RP-KID and reserve 6GHz
C. VM-K2 can be powered on because it can get the resources needed from RP-MOM
D. VM-K2 cannot be powered on because there are not enough resources in RP-KID.
E.
F.
G.
H.
I.
J.
解析:
A. Add a minimum of three hosts with two uplinks each
B. Add a minimum of two hosts with two uplinks each
C. Add a minimum of three hosts with four uplinks ea/ch
D. Add a minimum of two hosts with one uplink each
A. The virtual machine will be restored to the parent snapshot
B. The virtual machine will be restored in a powered off state
C. The virtual machine will be restored to the child snapshot
D. The virtual machine will be restored in a powered on state
E. The virtual machine will be restored in a suspended state
F.
G.
H.
I.
J.
解析:
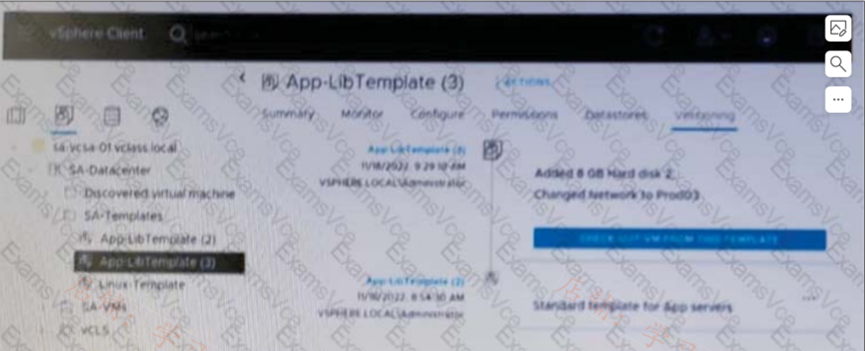 Given the configuration shown in the exhibit, what should the administrator do if the latest VM template contains changes that are no longer needed?
Given the configuration shown in the exhibit, what should the administrator do if the latest VM template contains changes that are no longer needed?
A. Delete App-LibTemplate (2)
B. Revert to App-LibTernplate (2)
C. Delete App-LibTemplate (3)
D. Check out App-LibTemplate (3)
解析:解析: Deleting App-LibTemplate (3) will remove the changes that are no longer needed and revert to the previous version of the template.删除App-LibTemplate (3)将删除不再需要的更改,并恢复到模板的前一版本。
A. Predictive DRS
B. Proactive HA
C. vSphere HA Orchestrated Restart
D. vSphere Fault Tolerance
E.
F.
G.
H.
I.
J.
解析:解释主动HA是一种群集功能,可用于在主机硬件运行状况降级时,在故障发生之前自动迁移虚拟机。
A. Extract the host profile from the reference host
B. Export the host profile from vCenter.
C. Import host customization on the reference host.
D. Attach the host profile to each cluster that requires the secure configuration.
E. Check the compliance of each host against the host profile.
F. Reset host customization on the reference host.
G. 在引用主机上重置主机定制。
H.
I.
J.
解析:解析: To apply the security standards from a reference host to other hosts across multiple clusters, the administrator needs to extract a host profile from the reference host, which captures its configuration settings; attach the host profile to each cluster that requires the same configuration; check the compliance of each host against the host profile, which compares their settings; and remediate all non-compliant hosts, which applies the configuration settings from the host profile.为了将来自参考主机的安全标准应用到跨多个集群的其他主机,管理员需要从参考主机提取主机配置文件,该主机配置文件捕获其配置设置;将主机配置文件附加到需要相同配置的每个群集;对照主机配置文件检查每台主机的合规性,主机配置文件会比较它们的设置;并修复所有不符合的主机,这将应用主机配置文件中的配置设置。