

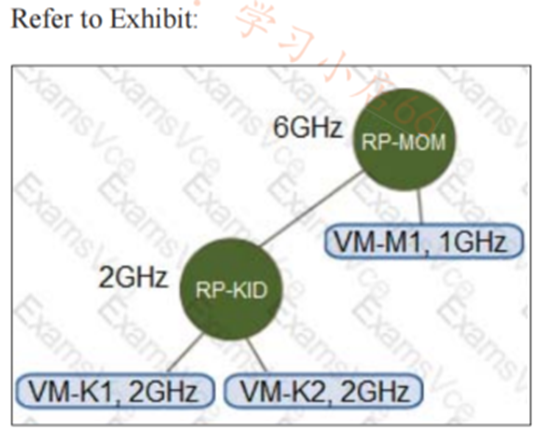
 An environment has the following configuration: •Resource Pool “RP-MOM? has a reservation of 6GHz and one running virtual machine (VM) ”VM-M1? With 1 GHz reserved •Resource Pool ^RP-KID? has a reservation of 2GHz, and expandable reservations is activated The administrator creates two VMs, “VM-K1? and 'VM-K2?, in the ''RP-KID? resource pool with 2GHz reserved for each, and turns on “VM-M1 ?
An environment has the following configuration: •Resource Pool “RP-MOM? has a reservation of 6GHz and one running virtual machine (VM) ”VM-M1? With 1 GHz reserved •Resource Pool ^RP-KID? has a reservation of 2GHz, and expandable reservations is activated The administrator creates two VMs, “VM-K1? and 'VM-K2?, in the ''RP-KID? resource pool with 2GHz reserved for each, and turns on “VM-M1 ?
A、 The administrator must deactivate expandable reservations to turn on VM-K2
B、 The administrator can create a third VM ( VM-K3?) at RP-KID and reserve 6GHz
C、 VM-K2 can be powered on because it can get the resources needed from RP-MOM
D、 VM-K2 cannot be powered on because there are not enough resources in RP-KID.
E、
F、
G、
H、
I、
J、
答案:C
解析:



 An environment has the following configuration: •Resource Pool “RP-MOM? has a reservation of 6GHz and one running virtual machine (VM) ”VM-M1? With 1 GHz reserved •Resource Pool ^RP-KID? has a reservation of 2GHz, and expandable reservations is activated The administrator creates two VMs, “VM-K1? and 'VM-K2?, in the ''RP-KID? resource pool with 2GHz reserved for each, and turns on “VM-M1 ?
An environment has the following configuration: •Resource Pool “RP-MOM? has a reservation of 6GHz and one running virtual machine (VM) ”VM-M1? With 1 GHz reserved •Resource Pool ^RP-KID? has a reservation of 2GHz, and expandable reservations is activated The administrator creates two VMs, “VM-K1? and 'VM-K2?, in the ''RP-KID? resource pool with 2GHz reserved for each, and turns on “VM-M1 ?
A、 The administrator must deactivate expandable reservations to turn on VM-K2
B、 The administrator can create a third VM ( VM-K3?) at RP-KID and reserve 6GHz
C、 VM-K2 can be powered on because it can get the resources needed from RP-MOM
D、 VM-K2 cannot be powered on because there are not enough resources in RP-KID.
E、
F、
G、
H、
I、
J、
答案:C
解析:


A. Forged transmits set to reject
B. MAC address changes set to accept
C. Promiscuous mode set to reject
D. Promiscuous mode set to accept
解析:解析:The security policy that must be configured at the port group level to allow all traffic to be forwarded regardless of the destination is promiscuous mode set to accept, which allows receiving all traffic on a virtual switch port.必须在端口组级别配置安全策略,以允许转发所有流量,而不管目的地是哪里,将混杂模式设置为接受,这允许在虚拟交换机端口上接收所有流量。
A. vSphere vMotion
B. PCI passthrough
C. vSphere High Availability (HA)
D. vSphere Fault Tolerance
E. vSphere Distributed Resources Scheduler (DRS)
F. Hot Add of CPU or memory
G.
H.
I.
J.
解析:解析: Option A, C and E are correct because they indicate that vSphere features such as vMotion, High Availability (HA) and Distributed Resource Scheduler (DRS) are still supported for Windows-based virtual machines when enabling vSphere’s virtualization-based security feature, which provides enhanced protection for guest operating systems and applications against various attacks. Option B is incorrect because PCI passthrough is not supported for Windows-based virtual machines when enabling vSphere’s virtualization-based security feature, as this feature requires direct access to physical devices that cannot be shared or protected by hypervisor mechanisms. Option D is incorrect because Fault Tolerance is not supported for Windows-based virtual machines when enabling vSphere’s virtualization-based security feature, as this feature requires identical execution states for primary and secondary virtual machines that cannot be guaranteed by hypervisor mechanisms. Option F is incorrect because Hot Add of CPU or memory is not supported for Windows-based virtual machines when enabling vSphere’s virtualization-based security feature, as this feature requires dynamic changes to virtual hardware configuration that cannot be handled by hypervisor mechanisms.解释选项A、C和E是正确的,因为它们表明,在启用vSphere基于虚拟化的安全功能时,基于Windows的虚拟机仍然支持vMotion、高可用性(HA)和分布式资源调度器(DRS)等vSphere功能,该功能为来宾操作系统和应用程序提供了增强的保护,可抵御各种攻击。选项B不正确,因为在启用vSphere基于虚拟化的安全功能时,基于Windows的虚拟机不支持PCI直通,因为该功能需要直接访问无法由虚拟机管理程序机制共享或保护的物理设备。选项D不正确,因为在启用vSphere基于虚拟化的安全功能时,基于Windows的虚拟机不支持容错,因为该功能要求主虚拟机和辅助虚拟机具有相同的执行状态,而虚拟机管理程序机制无法保证这一点。选项F不正确,因为在启用vSphere基于虚拟化的安全功能时,基于Windows的虚拟机不支持热添加CPU或内存,因为该功能需要对虚拟硬件配置进行动态更改,而虚拟机管理程序机制无法处理这些更改。
A. Encrypted vSphere vMotion
B. Unified Extensible Firmware Interface (UEFI) Secure Boot
C. Host Encryption
D. VM Encryption
解析:解析: The feature that should be configured to provide encryption for workloads within an existing vSphere cluster without requiring any specific hardware is VM Encryption, which allows encrypting VMs at rest and during vMotion.在不需要任何特定硬件的情况下,为现有vSphere群集中的工作负载提供加密应该配置的功能是虚拟机加密,它允许在静态和vMotion期间加密虚拟机。
A. Remove PROD01 and create a new VMkernel port and set the TCP/IP stack to vSphere vMotion.
B. Remove PROD01 and create a new VMkernel port with the TCP/IP stack set to provisioning
C. Create a new VMkernel port and set the TCP/IP stack to provisioning.
D. Modify PROD01 by changing the TCP/IP stack to vSphere vMotion.
E.
F.
G.
H.
I.
J.
解析:解析: Select a TCP/IP stack from the list. Once you set a TCP/IP stack for the VMkernel adapter, you cannot change it later. If you select the vMotion or the Provisioning TCP/IP stack, you will be able to use only these stacks to handle vMotion or Provisioning traffic on the host. All VMkernel adapters for vMotion on the default TCP/IP stack are disabled for future vMotion sessions. If you set the Provisioning TCP/IP stack, VMkernel adapterson the default TCP/IP stack are disabled for operations that include Provisioning traffic, such as virtual machine cold migration, cloning, and snapshot migration.从列表中选择一个TCP/IP堆栈。一旦为VMkernel适配器设置了TCP/IP堆栈,以后就不能再更改了。如果您选择vMotion或配置TCP/IP堆栈,您将只能使用这些堆栈来处理主机上的vMotion或配置流量。默认TCP/IP堆栈上用于vMotion的所有VMkernel适配器对于将来的vMotion会话都是禁用的。如果您设置了配置TCP/IP堆栈,默认TCP/IP堆栈上的VMkernel适配器将对包括配置流量的操作(如虚拟机冷迁移、克隆和快照迁移)禁用。
A. Use the Stage and Install option to resume the staging.
B. Use the Resume option to resume the staging.
C. Use the Unstage option to restart the staging.
D. Use the Stage Only option to restart the staging.
A. Apply Global permissions to assign the Read Only role to the root vCenter object.Apply vCenter permissions to assign the custom role to the workload vSphere clusters and enable propagation
B. Apply Global permissions to assign the Read Only role to the root vCenter object and enable propagation. Apply vCenter permissions to assign the custom role to the workload vSphere clusters and enable propagation
C. Apply Global permissions to assign the Read Only role to the root vCenter object. Apply vCenter permissions to assign the custom role to the workload vSphere clusters.
D. Apply Global permissions to assign the Read Only role to the root vCenter object and enable propagation. Apply vCenter permissions to assign the custom role to the workload vSphere clusters.
解析:解析: Option D is correct because it allows the administrator to apply Global permissions to assign the Read Only role to the root vCenter object and enable propagation, which will apply to all of the inventory objects in vCenter, and then apply vCenter permissions to assign the custom role to the workload vSphere clusters, which will override the Global permissions and allow users to edit all of the inventory objects associated with the workload vSphere clusters. Option A is incorrect because it will not enable propagation for the Global permissions, which will limit the Read Only role to the root vCenter object only. Option B is incorrect because it will enable propagation for both the Global and vCenter permissions, which will create a conflict between the Read Only and custom roles. Option C is incorrect because it will not enable propagation for either the Global or vCenter permissions, which will limit the Read Only role to the root vCenter object only and the custom role to the workload vSphere clusters only.选项D是正确的,因为它允许管理员应用全局权限将只读角色分配给根vCenter对象并启用传播,这将应用于vCenter中的所有清单对象,然后应用vCenter权限将自定义角色分配给工作负载vSphere群集,这将覆盖全局权限并允许用户编辑与工作负载vSphere群集关联的所有清单对象。选项A不正确,因为它不会启用全局权限的传播,从而将只读角色仅限于根vCenter对象。选项B不正确,因为它将启用全局和vCenter权限的传播,这将在只读和自定义角色之间产生冲突。选项C是不正确的,因为它不会为全局或vCenter权限启用传播,这会将只读角色仅限于根vCenter对象,将自定义角色仅限于工作负载vSphere群集。
A. Storage Policy Based Management
B. Storage I/O Control
C. vSphere Storage APIs for Storage Awareness (VASA)
D. vSphere Distributed Resource Scheduler (DRS)
A. Create a 'Must run Virtual Machines to Hosts' anti-affinity rule.
B. Create a 'Virtual Machines to Virtual Machines' anti-affinity rule.
C. Create a 'Virtual Machines to Virtual Machines' dependency rule.
D. Create a 'Should run Virtual Machines to Hosts' anti-affinity rule.
E.
F.
G.
H.
I.
J.
解析:
A. Configure vSphere Lifecycle Manager with an image for the cluster
B. Register the vendor hardware management system as a vCenter Server extension.
C. Download the firmware updates from the VMware website
D. Download the firmware updates from the vendor website.
E. Run a hardware compatibility check using vSphere Lifecycle Manager
F. Configure vSphere Lifecycle Manager with a baseline for the cluster.
G.
H.
I.
J.
解析:The administrator should take these three steps to perform an update to vSphere clusters that are running vSAN: Configure vSphere Lifecycle Manager with an image for the cluster, which allows the administrator to specify the desired ESXi version and firmware for the hosts in the cluster. Register the vendor hardware management system as a vCenter Server extension, which allows the administrator to update the firmware on the hosts using vSphere Lifecycle Manager. The vendor hardware management system can also provide the firmware updates to vSphere Lifecycle Manager, so there is no need to download them from the vendor website separately. Run a hardware compatibility check using vSphere Lifecycle Manager, which verifies that the new software and firmware versions are compatible with the vSAN Hardware Compatibility List.管理员应采取以下三个步骤来对运行vSAN的vSphere集群执行更新:使用集群映像配置vSphere Lifecycle Manager,这允许管理员为集群中的主机指定所需的ESXi版本和固件。将供应商硬件管理系统注册为vCenter Server扩展,这允许管理员使用vSphere Lifecycle Manager更新主机上的固件。供应商硬件管理系统还可以向vSphere Lifecycle Manager提供固件更新,因此无需单独从供应商网站下载。使用vSphere Lifecycle Manager运行硬件兼容性检查,验证新的软件和固件版本是否与vSAN硬件兼容性列表兼容。
A. sphere Update Manager
B. VMware Aria Suite Lifecycle
C. vCenter Server Update Planner
D. vSphere Lifecycle Manager
解析:解析: The tool that can be used to run interoperability reports before upgrading a vCenter Server instance is vCenter Server Update Planner, which allows checking compatibility with other VMware products.可用于在升级vCenter Server实例之前运行互操作性报告的工具是vCenter Server Update Planner,它允许检查与其他VMware产品的兼容性。