

A、 vSphere Virtual Machine Encryption
B、 vSphere Visualization-Based Security
C、 Virtual Intel Software Guard Extensions (vSGX)
D、 Virtual Trusted Platform Module (vTPM)
E、
F、
G、
H、
I、
J、
答案:C
解析:



A、 vSphere Virtual Machine Encryption
B、 vSphere Visualization-Based Security
C、 Virtual Intel Software Guard Extensions (vSGX)
D、 Virtual Trusted Platform Module (vTPM)
E、
F、
G、
H、
I、
J、
答案:C
解析:


A. Configure vSphere Lifecycle Manager with an image for the cluster
B. Register the vendor hardware management system as a vCenter Server extension.
C. Download the firmware updates from the VMware website
D. Download the firmware updates from the vendor website.
E. Run a hardware compatibility check using vSphere Lifecycle Manager
F. Configure vSphere Lifecycle Manager with a baseline for the cluster.
G.
H.
I.
J.
解析:The administrator should take these three steps to perform an update to vSphere clusters that are running vSAN: Configure vSphere Lifecycle Manager with an image for the cluster, which allows the administrator to specify the desired ESXi version and firmware for the hosts in the cluster. Register the vendor hardware management system as a vCenter Server extension, which allows the administrator to update the firmware on the hosts using vSphere Lifecycle Manager. The vendor hardware management system can also provide the firmware updates to vSphere Lifecycle Manager, so there is no need to download them from the vendor website separately. Run a hardware compatibility check using vSphere Lifecycle Manager, which verifies that the new software and firmware versions are compatible with the vSAN Hardware Compatibility List.管理员应采取以下三个步骤来对运行vSAN的vSphere集群执行更新:使用集群映像配置vSphere Lifecycle Manager,这允许管理员为集群中的主机指定所需的ESXi版本和固件。将供应商硬件管理系统注册为vCenter Server扩展,这允许管理员使用vSphere Lifecycle Manager更新主机上的固件。供应商硬件管理系统还可以向vSphere Lifecycle Manager提供固件更新,因此无需单独从供应商网站下载。使用vSphere Lifecycle Manager运行硬件兼容性检查,验证新的软件和固件版本是否与vSAN硬件兼容性列表兼容。
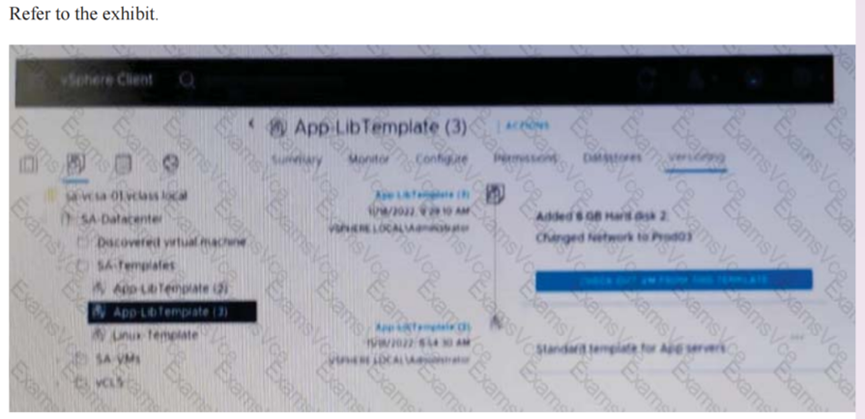 Given the configuration shown in the exhibit, what must the administrator do to delete only the latest version of the template?
Given the configuration shown in the exhibit, what must the administrator do to delete only the latest version of the template?
A. Delete App-LibTemplete(3) from the SA-Templates folder.
B. In the SA-template folder, rename App-Libtemplate (2) to App-LibTemplate
C. Check out AppLibTemplate (3) and delete the template from the SA-Templates folder.
D. Revert to APP-LibTemplate (2) and delete App-LibTemplate (3).
解析:解析: Option D is correct because it allows the administrator to delete only the latest version of the template by reverting to the previous version and then deleting the current version. Option A is incorrect because it deletes the entire template and not just the latest version. Option B is incorrect because it renames the previous version to the current version and does not delete anything. Option C is incorrect because it checks out the latest version and deletes it from the folder, but not from the library.选项D是正确的,因为它允许管理员通过恢复到先前版本然后删除当前版本来仅删除模板的最新版本。选项A不正确,因为它删除了整个模板,而不仅仅是最新版本。选项B不正确,因为它将以前的版本重命名为当前版本,并且不删除任何内容。选项C不正确,因为它会检出最新版本并将其从文件夹中删除,而不是从库中删除。
A. Medium
B. Tiny
C. Large
D. Small
解析:解析:VMWare: Small environment (up to 100 hosts or 1,000 virtual machines) Medium environment (up to 400 hosts or 4,000 virtual machine)The administrator should select the small deployment size for the new vCenter Server instance, which is suitable for an environment with up to 100 hosts or 1,000 virtual machines. The small deployment size has 4 vCPUs and 19 GB of memory, which can handle the current and expected growth of the environment. The other deployment sizes are either too large or too small for the environment.VMWare:小型环境(最多100台主机或1,000台虚拟机)中型环境(最多400台主机或4,000台虚拟机)管理员应为新的vCenter Server实例选择小型部署,这适用于最多100台主机或1,000台虚拟机的环境小型部署有4个vCPUs和19 GB内存,可以处理环境的当前和预期增长。其他部署规模对于环境来说要么太大,要么太小。
A. Ensure that the source and destination vCenter instances share the same Key Management Server (KMS).
B. Ensure that Encrypted vMotion Is turned off for the VM
C. Ensure that the VM is encrypted before attempting the migration
D. Ensure that the VM is powered off before attempting the migration.
E. Ensure that the source and destination vCenter Servers have a different Key Management Server (KMS).
F.
G.
H.
I.
J.
解析:解析: To ensure a successful migration of an encrypted VM to a secure environment, the administrator needs to ensure that the source and destination vCenter instances share the same Key Management Server (KMS), which provides encryption keys for both environments; and ensure that the VM is encrypted before attempting the migration, which allows preserving its encryption status during vMotion.为了确保加密虚拟机成功迁移到安全环境,管理员需要确保源和目标vCenter实例共享同一个密钥管理服务器(KMS),该服务器为两个环境提供加密密钥;并确保在尝试迁移之前对虚拟机进行加密,这样可以在vMotion过程中保留其加密状态。
A. VMware Horizon
B. VMware vSAN
C. VMware vSphere
D. VMware
解析:解析:Option C is correct because VMware vSphere is the solution that provides a software-defined data center platform that can consolidate physical servers by migrating the workloads to virtual machines. Option A is incorrect because VMware Horizon is a solution for virtual desktop infrastructure (VDI) and application delivery. Option B is incorrect because VMware vSAN is a solution for software-defined storage that is integrated with vSphere. Option D is incorrect because VMware NSX is a solution for software-defined Networking that is integrated with vSphere.选项C是正确的,因为VMware vSphere是提供软件定义的数据中心平台的解决方案,该平台可以通过将工作负载迁移到虚拟机来整合物理服务器。选项A不正确,因为VMware Horizon是虚拟桌面基础架构(VDI)和应用交付的解决方案。选项B不正确,因为VMware vSAN是一种与vSphere集成的软件定义的存储解决方案。选项D不正确,VMware NSX是一种与vSphere集成的软件定义网络解决方案。
A. Predictive DRS
B. Proactive HA
C. vSphere HA Orchestrated Restart
D. vSphere Fault Tolerance
E.
F.
G.
H.
I.
J.
解析:解释主动HA是一种群集功能,可用于在主机硬件运行状况降级时,在故障发生之前自动迁移虚拟机。
A. Ensure a DNS A Record is created for the VMware ESXi host on the corporate DNS servers.
B. Update the VMware ESXi Management Network DNS configuration to use the corporate DNS servers for names resolution
C. Update the VMware ESXi Management Network IPv4 configuration to use a static a IPv4 address
D. Configure at least two network adapters for the VMware ESXi Management Network
E. Set the value of the VMware ESXi Management Network VLAN ID to 10
F. Disable IPv6 for the VMware ESXi Management Network
G.
H.
I.
J.
解析:
A. Apply Global permissions to assign the Read Only role to the root vCenter object.Apply vCenter permissions to assign the custom role to the workload vSphere clusters and enable propagation
B. Apply Global permissions to assign the Read Only role to the root vCenter object and enable propagation. Apply vCenter permissions to assign the custom role to the workload vSphere clusters and enable propagation
C. Apply Global permissions to assign the Read Only role to the root vCenter object. Apply vCenter permissions to assign the custom role to the workload vSphere clusters.
D. Apply Global permissions to assign the Read Only role to the root vCenter object and enable propagation. Apply vCenter permissions to assign the custom role to the workload vSphere clusters.
解析:解析: Option D is correct because it allows the administrator to apply Global permissions to assign the Read Only role to the root vCenter object and enable propagation, which will apply to all of the inventory objects in vCenter, and then apply vCenter permissions to assign the custom role to the workload vSphere clusters, which will override the Global permissions and allow users to edit all of the inventory objects associated with the workload vSphere clusters. Option A is incorrect because it will not enable propagation for the Global permissions, which will limit the Read Only role to the root vCenter object only. Option B is incorrect because it will enable propagation for both the Global and vCenter permissions, which will create a conflict between the Read Only and custom roles. Option C is incorrect because it will not enable propagation for either the Global or vCenter permissions, which will limit the Read Only role to the root vCenter object only and the custom role to the workload vSphere clusters only.选项D是正确的,因为它允许管理员应用全局权限将只读角色分配给根vCenter对象并启用传播,这将应用于vCenter中的所有清单对象,然后应用vCenter权限将自定义角色分配给工作负载vSphere群集,这将覆盖全局权限并允许用户编辑与工作负载vSphere群集关联的所有清单对象。选项A不正确,因为它不会启用全局权限的传播,从而将只读角色仅限于根vCenter对象。选项B不正确,因为它将启用全局和vCenter权限的传播,这将在只读和自定义角色之间产生冲突。选项C是不正确的,因为它不会为全局或vCenter权限启用传播,这会将只读角色仅限于根vCenter对象,将自定义角色仅限于工作负载vSphere群集。
A. The datastore contains Raw Device Mappings (RDMs)
B. SAS disks are used for the datastore
C. The datastore has multiple extents.
D. The datastore is using ISCSI.
E. The administrator is using NFS storage.
F.
G.
H.
I.
J.
解析:解析:SIOC configuration may fail if the datastore contains RDMs or has multiple extents, as these are not supported by SIOC.Storage I/O Control is supported on Fibre Channel-connected, iSCSI-connected, and NFS-connected storage. Raw Device Mapping (RDM) is not supported. Storage I/O Control does not support datastores with multiple extents.如果数据存储区包含RDM或有多个扩展区,SIOC配置可能会失败,因为SIOC不支持这些。F6-4光纤通道连接、iSCSI连接和NFS连接的存储支持存储I/O控制。不支持原始设备映射(RDM)。存储I/O控制不支持具有多个数据区的数据存储。
A. vSphere vMotion
B. Cross vCenter Migration
C. vSphere Storage vMotion
D. vSphere Fault Tolerance
解析:解析:vSphere vMotion allows for the non-disruptive migration of a virtual machine between two clusters in a single vCenter instance, as long as there is shared storage and network connectivity between the clusters.vMotion is used to move the VM to a different cluster within the same vCenter. This only works if both clusters share the same storage. If they don't you also need to perform a Storage vMotion. Cross vCenter Migration is only used to migrate to a different vCenter.只要群集之间存在共享存储和网络连接,vSphere vMotion就可以在单个vCenter实例中的两个群集之间无中断地迁移虚拟机。vMotion用于将虚拟机移动到同一vCenter内的不同群集。这只有在两个群集共享相同存储时才有效。如果没有,您还需要执行Storage vMotion。跨vCenter迁移仅用于迁移到不同的vCenter。